Choose a Security Operations Center as a Service (SOCaaS) plan or individual services to complement your IT team's capabilities.
Advanced Cyber Defense Technologies
Zones SOCaaS uses artificial and augmented intelligence, machine learning, and the latest threat feeds to defend your IT environment against cyberattacks.
As cybercrime tactics and techniques have evolved, they've become more targeted. More evasive. And defending against them has become more of a challenge, especially with the shift to remote employees and hybrid workplaces.
Cybersecurity is complex and demanding. An organization can receive thousands of security alerts every week. Overloaded in-house IT teams are struggling to keep up – leaving organizations vulnerable to data breaches and worse.
That's why many organizations now use the expertise of a managed security service provider (MSSP) – a certified security team that can identify risks, recommend remediation strategies, and more.



Zones Can Proactively Prevent, Detect, and Respond to Security Threats for You
As your MSSP, Zones can help you address problems in your day-to-day operations that hinder your organization's ability to protect against a data breach, malware, ransomware, and other cybersecurity threats.
Zones' cybersecurity experts offer unparalleled managed cybersecurity services on a global scale. From core security information and event management (SIEM) services to security orchestration, automation, and response (SOAR), we're here to help.
With SOCaaS, you'll get near real-time monitoring, advanced contextual analysis, and better visibility through customized reports and dashboards to proactively prevent, detect, and respond to security threats. Our user-friendly online portal makes it easy to view the security state classification of your assets, as well as alerts, incidents, and robust regulatory reporting tools at any time.
Our passion and expertise help give you the upper hand against cybercriminals.
Working remotely from a state-of-the-art Security Operations Center (SOC), our outstanding team of security analysts, engineers, and researchers are all accredited to the highest professional standards. We're passionate cybercrime fighters ready to help defend your IT environment against cybercriminals.
Benefits Overview
Working with Zones is a fraction of what you'd pay to hire an entire SOC team. We can reduce the burden on your in-house IT team, giving them more time to focus on mission-critical threats and initiatives.
The Zones SOC and SOCaaS give you flexible options and service plans. Benefits for your organization will vary based on your service needs but can include:
- More robust security posture with a reduced total cost of ownership (TCO)
- 24x7 availability of centralized reports and dashboards, including robust regulatory reporting tools
- Move costs from capital expense (CapEx) to operational expense (OpEx)
- Responsive service and quality delivery
- Flexible and scalable architecture
- Integrated security framework
- Effective monitoring and visibility
- Incident response support
- Threat intelligence and hunting
- User behavior analysis
- Network behavior and traffic analysis
- Universal anomaly detection
- Security orchestration and response
3 SOCaaS Plans to Choose From
Or request only the services you need
| Bronze | Silver | Gold | ||
| Automated SOC activities. Counter advanced threats with threat intelligence. | Adds moderate customization, extended SOC solutions, and Threat Intelligence backed by analytics. | Adds proactive and defensive services. Reduces operational and infrastructure costs to maintain SOC services. | ||
| Services | Service Description | |||
| Security Information and Event Management (SIEM) | Gathers and analyzes security events, contextual data sources and more to support threat detection, regulatory reporting, and security incident management. | |||
| Basic Threat Intelligence (TI) | Free threat intelligence feeds record and track IP addresses and URLs associated with phishing scams, malware, bots, trojans, adware, spyware, ransomware, and more. | |||
| TI + Management | Native integrations with 110+ TI sources (open source and commercial), and out-of-the-box integration with the Malware Information Sharing Platform (MISP) for faster threat detection and triage. | |||
| Network Behavior and Anomaly Detection (NBAD) | Continuously monitors your network for unusual events or trends. | |||
| Network Traffic Analysis (NTA) | Monitors network availability and activity; identifies anomalies that could affect security and operations. | |||
| User and Entity Behavior Analytics (UEBA) | Protects your data from the inside out by detecting behavioral anomalies across your IT landscape, including routers, servers, and endpoints. Protects against internal and external threats. | |||
| Sandbox for New and Advanced Persistent Threats (APTs) | Provides a proactive layer of network security defense. An APT uses continuous, sophisticated hacking techniques to compromise organizations and steal data. | |||
| Security Orchestration, Automation and Response (SOAR) | Enables you to collect inputs monitored by the Zones SOC team. | |||
| Deception | This technology is designed to deceive attackers by deploying traps and decoys within your network to imitate genuine assets. Doing so helps detect and defend against advanced threats. | |||
| Threat Hunting | Proactively and iteratively searching for cyberthreats that are lurking undetected in a network. |
How SOCaaS Works
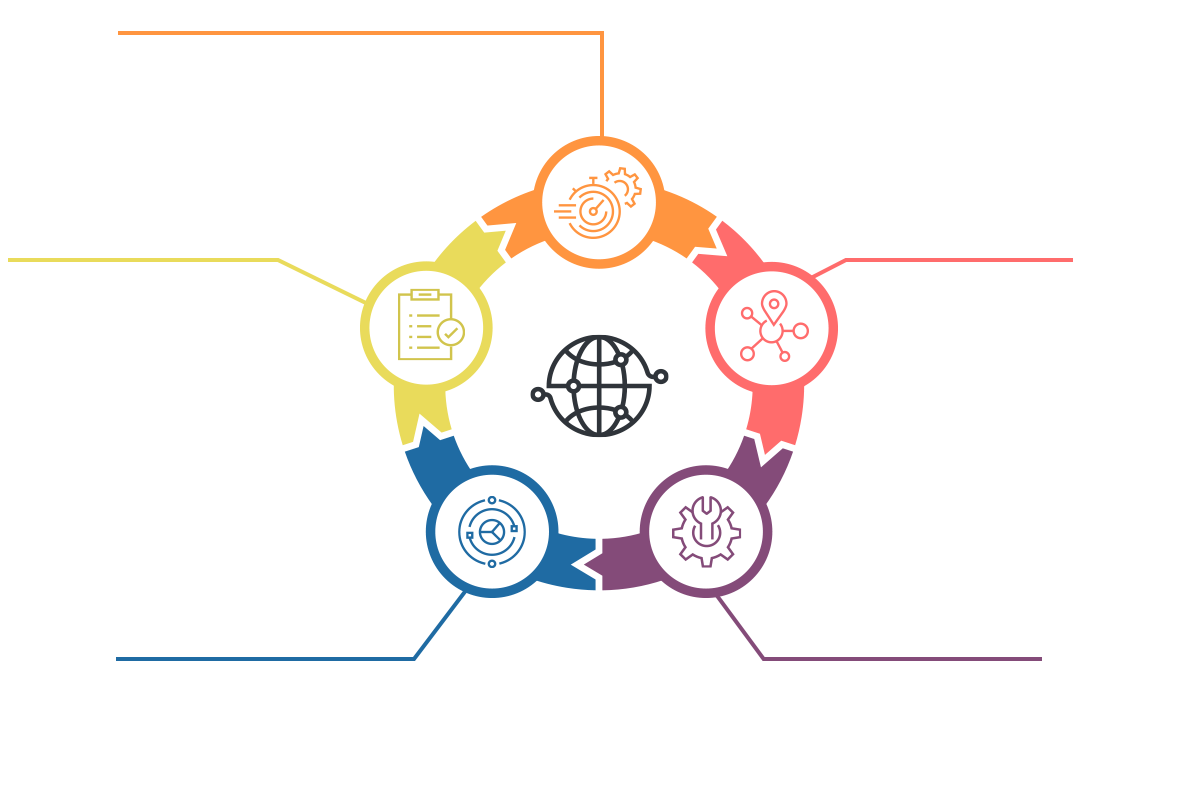
As your MSSP, Zones applies a proven cybersecurity framework to provide cohesive and comprehensive data protection.
Zones Cybersecurity Framework
With our SOCaaS, we start by parsing the logs from your network, devices, and security architecture through our cybersecurity analysis platform.
Using advanced cyber defense technologies, the platform and our SOC team will then:
Identify


Identify security and operational events in your IT environment by collecting log data.
Detect


Detect suspicious activity that our SOC needs to investigate.
Analyze


Analyze the collected log data, correlate events and alerts, and triage devices that are having an identified security incident.
Respond

Respond by notifying your security team according to our agreed-upon playbook and escalation matrix.
Remediate


Remediate the risk by advising your security team on remediation steps.
A Closer Look at Zones' SOC Capabilities
Continuous Proactive Monitoring
- 24x7x365 monitoring to address
abnormalities - Immediate notification of
emerging threats - Intelligent AI/ML-enabled operations
Optimized TCO
- Increased efficiency through
integration, automation
and orchestration - Reduced labor cost
- Centralized operations reduce
the burden of manual data sharing,
auditing, and reporting throughout - Expenses move from CapEx to OpEx
Remediation & Containment
- Restore systems and recover
any compromised data - Wipe and restart endpoints
- Reconfigure systems
Centralized Visibility
A complete view of your threat
landscape, including:
- Endpoints, servers and software
on premise - Third-party services
- Traffic flowing between these
assets
Preventative Maintenance
- Regular system maintenance and updates
- Update firewall policies and patch
vulnerabilities - Whitelisting and blacklisting
- Secure applications
We're Much More Than an MSSP
Zones is a global provider of comprehensive IT solutions with fulfillment capabilities across 100+ countries. In fact, we've been helping clients reap the benefits of technology for more than 35 years.
In addition to our in-house experts, we collaborate with industry-leading brands to deliver customizable solutions and positive business outcomes for our customers.
Zones is a certified Minority Business Enterprise (MBE) under the National Minority Supplier Development Council, Inc. (NMSDC) guidelines. We're also a certified Corporate Plus™ member of the NMSDC, recognizing our proven expertise in handling contracts for large and complex organizations.


We have the capabilities to deliver quality services at an affordable price.
- End-to-end IT service delivery expertise
- Well-defined service catalog to meet your business needs
- Award-winning Global Supply Chain as a Service (GSCaaS)
- Global network of offices, partners, and affiliates provides seamless support and services that ensure the integrity of your IT solutions
You can rely on us to collaborate and take the initiative to understand your business goals. It's part of our methodology to ensure you get the right solution for your needs while enjoying an outstanding customer experience.